Protection from spying and cybercriminals!
The ZUKKA platform offers state-of-the-art secure communication technology that enables our users to exchange information with complete confidence. By closing the main avenue for data breaches – often caused by a single weak link or human error – we prevent the leakage of sensitive information. This, in turn, helps protect your or your organization’s computer systems from being hacked. ZUKKA strengthens your security by ensuring that vulnerabilities are sealed before they can be exploited.
Today’s Challenge!
The security of computer systems is constantly improving but it is focused on implementing various security procedures and controls along with installing security software. However , this approach often overlooks the critical need to secure communications and sensitive data on all devices used by people in the organization
But, attacks continue to increase!
Cyber attacks are on the rise, largely because traditional street crime is increasingly collaborating with cyber crime. With the prevalence of smartphones today being a data vault, individuals are more vulnerable than ever, creating significant security challenges.
Stolen Device
Whether your phone is stolen or lost, your data remains secure and inaccessible with our advanced security solutions. Stay protected, no matter what!
Selling to a Cybercriminal
Your stolen phone can end up in the hands of a cybercriminal. With our security solutions, your data remains encrypted and useless to them, keeping your privacy intact.
Cracking the Device
A cybercriminal can easily extract sensitive data from your stolen phone, gaining quick access to your organization’s systems using credentials and cracked 2-factor authentication. Protect your devices and data with advanced security measures that stop them in their tracks.
THE solution!
At the forefront of innovation, we have created a groundbreaking secure communications platform that ensures your privacy is never compromised. Our system not only provides unhackable messaging, voice and video calling, but also allows you to seamlessly manage important confidential files (SecureBOX) from your mobile device.
By using our APP, you can replace traditional applications such as chat messengers, voice & video calls, file storage systems, password managers and secure storage solutions. What sets us apart is that all of your sensitive information is protected with advanced encryption, ensuring it remains out of reach even if your device is lost or stolen. Whether you’re communicating or managing critical data, our system delivers unmatched security, convenience, and peace of mind in an increasingly vulnerable digital world.
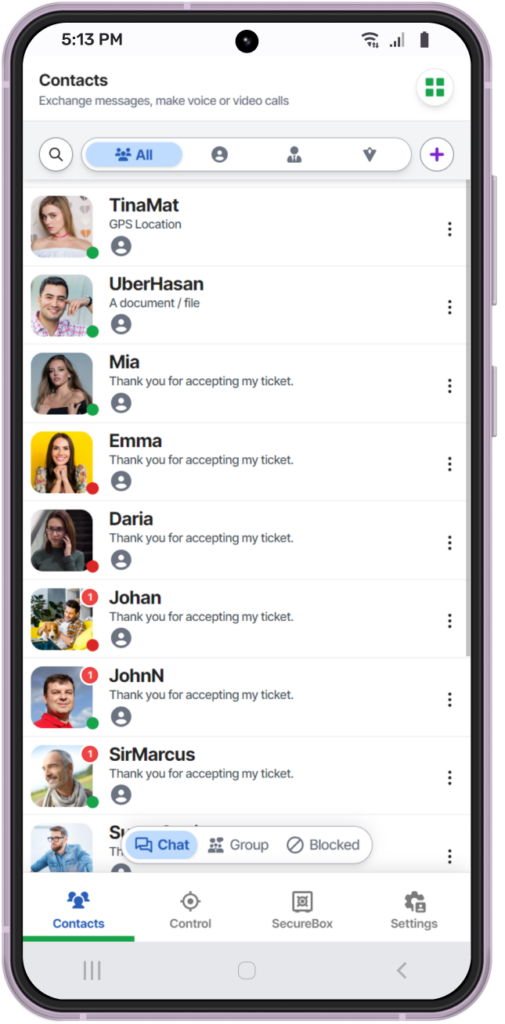
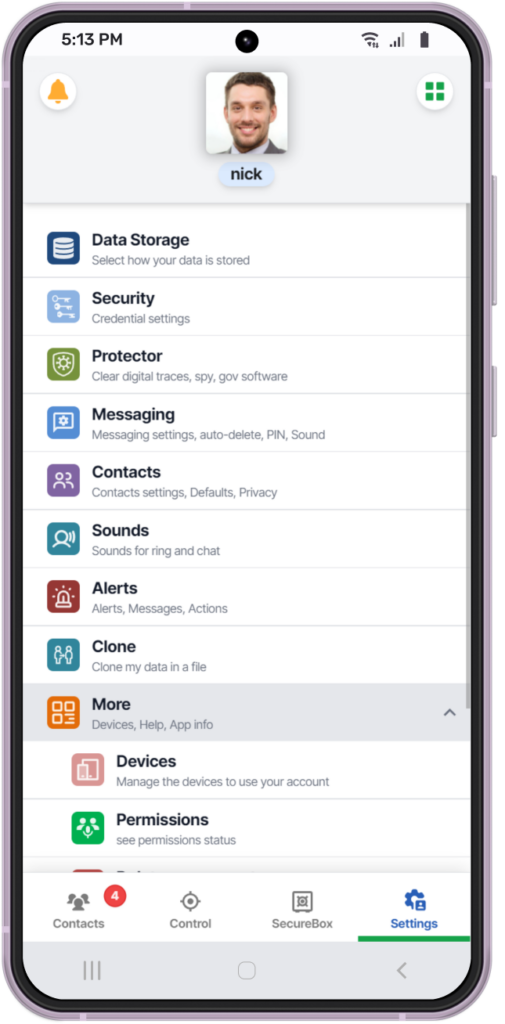
Unleash the Power:
The zukka IS:
The safest way to communicate in the world today, it keeps your communications out of the hands of hackers, companies and governments. It can be used completely anonymously and offers features you won’t find in any other instant messenger. It allows voice, video and group calls, encrypted much better than the usual end to end.
It’s just impossible to catch.
With ZUKKA, you receive a unique Ticket ID™ instead of an invite, ensuring zero spam and controlled, secure communication.
Your data is safely encrypted on the server, with encryption keys stored exclusively on your device, ensuring top-level privacy.
In case of loss, activate Panic Mode to delete all sensitive data from your device remotely, keeping your information secure.
Advanced encryption technology protects every interaction, ensuring confidentiality at every phase.
Store and manage sensitive files securely within the encrypted SecureBox feature.
Activate enhanced security with our Protected Confidentiality Mode for ultimate privacy during critical communications.
Stay protected with real-time alerts designed to keep your communication safe and secure.
Explore a wide range of additional security and privacy features designed to protect you from every angle.
SECTORS
ZUKKA is ideal for use across the following sectors, offered in flexible formats: APP, SAAS, On-Premise, or Customizable, depending on the specific needs of your organization.
This versatility ensures that organizations of all types can leverage our platform in a way that suits their unique operational and security requirements.

Government and Public Sector Bodies
With threats growing in complexity, government institutions must proactively address vulnerabilities and adopt strong cryptomessaging strategies. Our platform provides tailored solutions to enhance communication security and protect sensitive information, ensuring reliable protection against cyber threats.
ON-PREMISE
With our On-Premise solution, the entire server and data infrastructure is owned by your organization, ensuring maximum control and security.
Key features include:

Healthcare Providers
Healthcare organizations face rising cyberattack threats that jeopardize patient data, operational continuity, and regulatory compliance. Our platform offers a fully HIPAA-compliant cryptomessaging solution, ensuring that communications are both encrypted and secure to protect sensitive information.
Saas or ON-PREMISE
Our infrastructure can be deployed either as Software as a Service (SaaS) or as an On-Premise solution, giving your organization full ownership and control over your server and data. Key features include:

Small and Medium-sized Enterprises (SMEs)
We recognize the unique challenges faced by Small and Medium-sized Enterprises (SMEs) and are committed to empowering them with robust cryptomessaging solutions tailored to their budgets and operational needs. Our platform provides the security and reliability SMEs require to safeguard their communications effectively.
SaaS
Our server infrastructure operates as Software as a Service (SaaS), providing a flexible and scalable solution that allows you to access powerful features without the need for extensive on-premise resources.
Key features include:

Law Firms
We recognize the distinct cybersecurity challenges law firms encounter. Our solutions are designed to safeguard sensitive client data while ensuring full compliance with industry regulations, providing peace of mind in an increasingly complex threat landscape.
SaaS
Our server infrastructure operates as Software as a Service (SaaS), providing a flexible and scalable solution that allows you to access powerful features without the need for extensive on-premise resources.
Key features include:

Education Providers
We assist schools, colleges, and universities in safeguarding their data with comprehensive solutions that ensure regulatory compliance. Our platform empowers educational institutions to protect sensitive information while fostering a secure learning environment.
SaaS
Our server infrastructure operates as Software as a Service (SaaS), providing a flexible and scalable solution that allows you to access powerful features without the need for extensive on-premise resources.
Key features include:

Charities and Nonprofits
We prioritize the protection of personal information for donors and supporters, offering tailored solutions to ensure data security and regulatory compliance. Our platform enables charities and nonprofits to maintain trust while effectively managing sensitive information.
SaaS
Our server infrastructure operates as Software as a Service (SaaS), providing a flexible and scalable solution that allows you to access powerful features without the need for extensive on-premise resources.
Key features include:
Compliance Commitment
At Zukka, we prioritize compliance with essential legislation and guidelines to mitigate risks and ensure robust cybersecurity. Adhering to industry standards is vital for safeguarding data, and our solutions align with key compliance frameworks, including ISO 27001, NIS2, GDPR, and PCI DSS. This commitment not only enhances our security posture but also builds trust with our clients by ensuring their data is managed responsibly and securely.
GDPR is a comprehensive data protection law that applies to all companies processing personal data of EU citizens, regardless of their location.
ISO 27001 is an international standard that outlines the requirements for establishing, implementing, maintaining, and continually improving an Information Security Management.
PCI DSS is a set of security standards designed to protect cardholder data during credit card transactions.
NIS2 is an EU directive aimed at enhancing the cybersecurity and resilience of network and information systems across essential service providers and digital service providers.